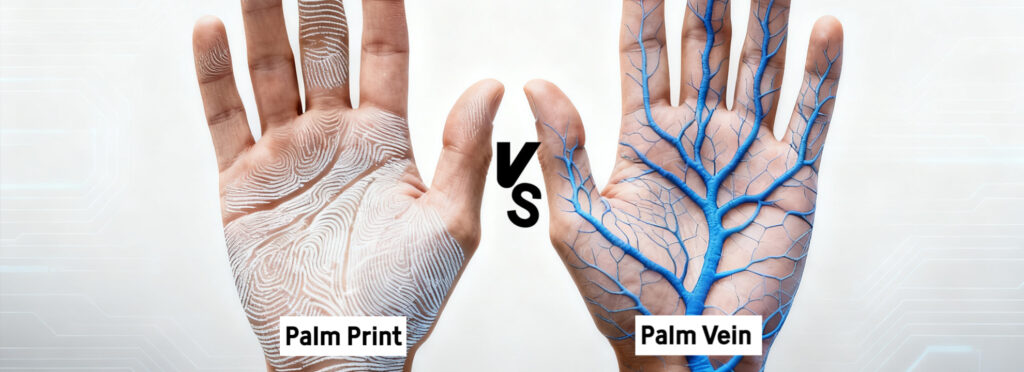
What Is an Iris Biometrics Scanner?
What Is an Iris Biometrics Scanner? Iris biometrics scanners are advanced identity verification devices that use the unique patterns in a person’s iris to confirm their identity. The iris, which is the colored ring around the pupil, contains intricate and stable patterns that remain unchanged throughout a person’s life. Because of this, iris recognition is […]