All You Need To Know About Face Access Control
Face access control is a type of security system that uses facial recognition to grant or deny access to a certain area. This technology can be used in both commercial and residential settings.
Face access control is a type of security system that uses facial recognition technology to identify and grant access to individuals. This system can be used to secure buildings, rooms, or even specific items. Face access control systems work by capturing an image of the person’s face and then comparing it to a database of known faces. If there is a match, then the person is granted access. If there is no match, then the person is denied access.
Purpose of Face Access Control
Face access control is a technology that uses facial recognition software to identify individuals and grant or deny them access to a particular area. This technology has been growing in popularity in recent years, as more and more businesses are looking for ways to improve security. There are many benefits of using face access control, including improved security, increased efficiency, and enhanced customer experience. In this blog post, we will discuss the purpose of face access control and how it can benefit your business!

1. Mayor seguridad para su negocio
Face access control can help you keep your business safe by preventing unauthorized personnel from gaining access to sensitive areas
2. Enhanced safety for employees
Face access control can also help you protect your employees by allowing them to quickly and easily identify authorized personnel.
3. Enhanced safety for customers
By using face access control, you can improve customer service by allowing customers to quickly and easily identify authorized personnel
4. Reduced liability risks
Face access control can help you reduce the risks associated with liability by allowing you to quickly and easily identify authorized personnel.
5. Easier identification
Face access control can help you quickly and easily identify authorized personnel in the event of an emergency
6. Cost-effective solution
Face access control can help you reduce costs by eliminating the need for physical keys or cards. In addition, face access control can improve the efficiency of your business by allowing you to quickly and easily identify authorized personnel.
Consideraciones al comprar un escáner de huellas dactilares
When it comes to choosing the right face access control device for your business, there are a few things you need to take into account
El tamaño del dispositivo
Debes asegurarte de que quepa cómodamente en tus manos y que no sea demasiado grande ni voluminoso.
donde comprarlos
Puede encontrarlos en línea , en tiendas o a través del fabricante. Si compra en línea, querrá asegurarse de comprarlo a un vendedor confiable.
Si compras en una tienda , podrás ver el escáner en persona y hacer preguntas sobre él.
Finalmente, si compra a través del fabricante , puede estar seguro de que obtendrá un producto de alta calidad.
Presupuesto
you need to decide how much you’re willing to spend on a face access control device.
Las características
Do you need a device that can scan multiple faces at once? Or do you need one that can read driver’s licenses?
Functions of Face Access Control
Check in / break out / break in/check out

Reconocimiento Facial
FACE++ is a cutting-edge facial recognition technology that powers some of the most popular apps and services on the market today. The technology can be used for a variety of purposes, including identity verification, security, and marketing. FACE++ relies on a combination of AI and machine learning to accurately identify individuals from images and videos. The technology is constantly improving, and it is now able to accurately identify people even when they are wearing masks or glasses. With its growing popularity, FACE++ is quickly becoming the standard for facial recognition technology.

IC Card
IC cards are becoming increasingly popular for use in access control systems. An IC card contains a microchip that stores information about the cardholder, such as their name, photograph, and contact details. This information can be used to verify the identity of the cardholder and grant them access to a particular area or building. Additionally, IC cards can be used to track the movement of people within a premises, and they can also be programmed to allow only certain types of entry at certain times. This makes them an ideal solution for businesses that need to tightly control access to their premises. In addition, IC cards are extremely durable and difficult to counterfeit, making them a secure option for businesses that need to protect their property and assets.

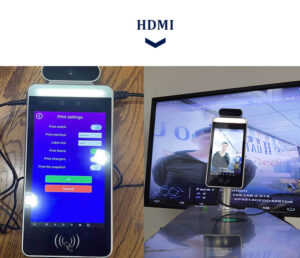
HDMI
HDMI (High-Definition Multimedia Interface) is a popular digital interface used to connect audio/video equipment. It is commonly used in home theater systems, gaming consoles, and computer monitors. HDMI can also be used in commercial applications, such as in access control systems. When used in an access control system, HDMI can provide high-quality video streaming and transmission, as well as audio support. This makes it a great option for businesses that need to transmit data between different locations. Additionally, HDMI is relatively easy to install and use, making it a cost-effective solution for businesses looking to improve their access control system.
Access control is a system that regulates who or what can view or use resources in a computing environment. It is a fundamental security measure that is used to protect information and systems from unauthorized access. One of the most common ways to implement access control is through the use of user IDs and passwords. However, this can be cumbersome and difficult to manage, especially in large organizations. An alternative approach is to use prints as a means of access control. This can be done by using fingerprint scanners or iris scanners to verify the identity of users before they are granted access to resources. This method is more secure than using user IDs and passwords, as it is more difficult to fake or guessing someone’s fingerprint or iris pattern. In addition, prints can also be used to track and audit user activity, which can be helpful in investigating security incidents. Thus, the use of prints for access control is a viable and effective alternative to traditional methods such as user IDs and passwords.

PDF417
PDF417 is a type of 2D barcode that can be used for a variety of applications, including access control. When used for access control, PDF417 can encode information such as an individual’s name, date of birth, and photograph. The barcode can then be read by an electronic reader, which can compare the encoded information to a database to verify the individual’s identity. PDF417 can also be used to track inventory or assets, and it is frequently used by businesses and government organizations for these purposes. Because PDF417 is a widely used standard, it is easy to integrate into existing access control systems. As a result, PDF417 is an ideal solution for businesses or organizations that need to secure their facilities and assets.

Medición de temperatura
Access control systems are used in a variety of settings, from office buildings to airports. One of the most important functions of an access control system is to measure the temperature of individuals as they pass through a security checkpoint. By doing so, security personnel can quickly identify individuals who may be suffering from a fever, which could indicate the presence of a contagious disease. In addition to measuring temperature, access control systems can also be used to scan for weapons or other prohibited items. As a result, they play an important role in keeping people safe and secure.

QR Code
A QR code is a quick response code that has the ability to store information. This information can be anything from a URL to contact information. A QR code can be read by a QR code reader which is readily available on many smartphones. More and more businesses are utilizing QR codes as a means of access control. For example, if you have a ticket to an event you may be able to scan the QR code on the ticket which will then give you access to the event. This is just one way businesses are using QR codes as an alternative to traditional methods such as key cards or ID badges. Another benefit of using QR codes for access control is that they are difficult to duplicate which helps to prevent fraud. Overall, QR codes offer a convenient and secure way for businesses to control access to their premises.

Questionnaire
Questionnaire function can be used in access control. When a new employee or a visitor enters the office, they can be asked to fill out a questionnaire. The questions can be about their purpose of visit, where they need to go, and who they need to see. This information can be used to generate a badge with their photo and name. The badge can be scanned when they enter and exit the building. This will help to keep track of who is coming and going, and it will also help to ensure that only authorized people are able to enter the building. In addition, the questionnaire can also be used to collect other important information, such as emergency contact information.

Palm
Palm scanners are becoming increasingly popular for use in access control applications. Unlike finger scanners, which require contact with the sensor, palm scanners can be used from a distance of up to six inches. This makes them ideal for use in high-traffic areas, where it would be impractical to stop and scan every person’s finger. In addition, palm scanners are more accurate than finger scanners, making them less likely to generate false positives. As a result, palm scanners are an effective and convenient way to control access to buildings and other secure areas.

Sensor de huellas dactilares
Fingerprint sensors have become increasingly commonplace in recent years, appearing in everything from smartphones to door locks. While the technology is often used for convenience, it can also offer a high level of security. In particular, fingerprint sensors are often used in access control systems. When used in this way, the sensor is able to confirm the identity of the person trying to gain entry, and only allow access if the fingerprint matches one that has been registered in the system. This makes it impossible for unauthorized individuals to enter, even if they have a copy of the key or know the code. As a result, fingerprint sensors can provide a high level of security for businesses and other sensitive locations.

Password
Password function can be used in access control to provide an extra layer of security. By requiring a password to log in, unauthorized users will be unable to access the system. In addition, passwords can be used to restrict access to certain features or information. For example, a user may only be able to view certain reports if they know the password. This can help to prevent sensitive information from falling into the wrong hands. passwords can also be used to track who is accessing what information. This can be helpful in auditing or troubleshooting problems. Overall, the use of passwords in access control can provide an extra level of security and protection.
NFC
Access control is an important security measure for any business or organization. It helps to ensure that only authorized personnel are able to enter a premises, and it can also be used to track and monitor employee activity. One way to create an access control system is to use NFC (Near Field Communications) tags. NFC tags are small devices that can be attached to ID cards, key fobs, or other objects. When an NFC-enabled device, such as a smartphone, is held up to the tag, it will communicate with the tag and provide information about the user. This information can then be used to grant or deny access to a building or area. NFC tags are a convenient and affordable way to create an access control system, and they can offer a high level of security for any business or organization.
Open Door
A common type of access control system is the open door function. This allows people to enter a building without requiring them to swipe their card or key in a code. Instead, they simply need to push a button or turn a handle. The open door function is often used in schools, hospitals, and other public buildings where there is a high volume of traffic. It is also used in office buildings and other commercial properties. The main advantage of the open door function is that it eliminates the need for people to carry around cards or keys. It also saves time, as people can enter the building without having to stop and swipe their card. However, the open door function also has some drawbacks. It can be easy to forget to push the button or turn the handle, which can result in people being locked out of the building. Additionally, the open door function can be used by unauthorized people to enter a building. For this reason, it is important to have an access control system that includes other security measures, such as CCTV cameras and security guards.
Close Door
The “Close Door” function is often used in conjunction with an access control system to ensure that doors are properly closed and secured. When this function is enabled, the system will automatically close the door after a certain period of time. This can be helpful in preventing unauthorized access, as well as in keeping pests and other unwanted guests out of your facility. In addition, the “Close Door” function can also help to conserve energy by preventing heat from escaping through open doors. When used properly, the “Close Door” function can be an effective tool for security and energy efficiency.
Alcohol
Alcohol is often used as a tool for controlling access to certain areas or events. For example, many clubs and bars use alcohol as a way to screening guests and ensure that only those over the legal drinking age are allowed entry. This can help to create a safe and enjoyable environment for patrons and staff alike. In addition, alcohol can also be used to control access to VIP areas or exclusive events. By requiring guests to purchase drinks, businesses can ensure that only those who are willing to spend the extra money are given access to the most sought-after areas. This can help to create a more upscale atmosphere and generate additional revenue. Ultimately, alcohol is a versatile tool that can be used to control access in a variety of different settings.

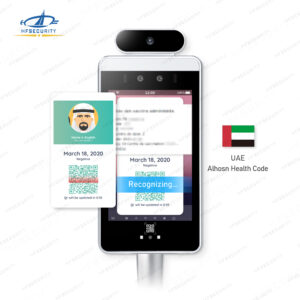
Escanéo de Código de Salud
The “Close Door” function is often used in conjunction with an access control system to ensure that doors are properly closed and secured. When this function is enabled, the system will automatically close the door after a certain period of time. This can be helpful in preventing unauthorized access, as well as in keeping pests and other unwanted guests out of your facility. In addition, the “Close Door” function can also help to conserve energy by preventing heat from escaping through open doors. When used properly, the “Close Door” function can be an effective tool for security and energy efficiency.