Gate access control solutions are integral components of modern security strategies, offering enhanced protection, convenience, and peace of mind. By understanding their features, benefits, and best practices, organizations can effectively deploy these systems to safeguard their premises and assets.
What is Gate Access Control?
Gate access control refers to the use of various technologies and systems to regulate and manage entry and exit points, typically at gates or barriers. These systems are designed to control who can enter a particular area, such as a residential community, commercial property, or industrial facility, by verifying the identity of individuals and granting or denying access accordingly. Gate access control solutions can include methods such as keypad entry, card readers, biometric systems (like fingerprint or facial recognition), or a combination of these technologies. The primary purpose of gate access control is to enhance security by preventing unauthorized access, protecting assets, and ensuring the safety of individuals within the controlled area.
Understanding Gate Access Control
Gate access control systems are designed to regulate and manage entry and exit points, typically at gates or barriers, by employing various technologies and components to authenticate individuals and grant or deny access accordingly. The primary purpose of these systems is to enhance security by preventing unauthorized access to a controlled area, thereby protecting assets and ensuring the safety of individuals within that area.
Gate Access Control Systems Serve Several Key purposes:
- 安全: The primary function of gate access control systems is to enhance security by allowing only authorized individuals to enter a specific area. By verifying the identity of individuals seeking access, these systems prevent unauthorized entry and reduce the risk of theft, vandalism, or other security breaches.
- Access Management: Gate access control systems enable organizations to manage access permissions for different individuals or groups. Administrators can define who is allowed to enter specific areas and under what conditions, ensuring that access is granted only to authorized personnel.
- Visitor Management: Many gate access control systems include features for managing visitor access, such as temporary passes or guest credentials. This allows organizations to monitor and regulate visitor traffic, ensuring that guests are authorized and properly escorted while on the premises.
- 監査証跡: Gate access control systems maintain detailed logs of access events, including information such as the date, time, and identity of individuals who accessed the area. These audit trails are valuable for security monitoring, compliance purposes, and investigative efforts following security incidents.
- 利便性: In addition to enhancing security, gate access control systems can also improve convenience for authorized users. By automating the entry process and eliminating the need for manual intervention, these systems streamline access procedures and reduce wait times for individuals entering or exiting a controlled area.
- 統合: Gate access control systems can integrate with other security systems and technologies, such as surveillance cameras, alarms, and building management systems. Integration enables organizations to create a comprehensive security infrastructure that provides enhanced protection and enables coordinated responses to security events.
Overall, gate access control systems play a crucial role in safeguarding facilities, properties, and assets by controlling access and ensuring that only authorized individuals can enter designated areas.
Types of Gate Access Control Solutions
Gate access control solutions come in various forms, each employing different technologies and methods for authentication and verification. Here are some common types of gate access control solutions:
- Keypad Entry Systems: Keypad entry systems require users to enter a unique PIN code on a keypad to gain access. The system verifies the entered code against a database of authorized codes, granting access if a match is found. Keypad entry systems are relatively simple and cost-effective but may be less secure than other methods if PIN codes are easily guessed or shared.
- カードリーダー: Card reader systems use proximity cards, smart cards, or key fobs containing electronic credentials to grant access. Users present their card or key fob to a card reader, which reads the electronic data stored on the card and verifies it against a database of authorized users. Card reader systems offer convenience and can easily manage access permissions for large numbers of users.
- Biometric Systems: Biometric access control systems use unique physical characteristics, such as fingerprints, iris patterns, or facial features, to authenticate users. Biometric data is captured and compared against stored templates to verify identity. Biometric systems offer high levels of security and eliminate the need for physical credentials, but they can be more expensive to implement and may encounter issues with accuracy and reliability in certain environments.
- Remote Control Systems: Remote control systems allow authorized users to control gate access remotely using mobile devices or computer networks. These systems typically involve electronic gate openers or barriers that can be operated via wireless signals, such as RFID or Bluetooth. Remote control systems offer flexibility and convenience, especially for gated communities or commercial properties with frequent visitors.
- Intercom Systems: Intercom systems incorporate audio and sometimes video communication between the gate and a central monitoring station or residence. Visitors must request entry via the intercom, and authorized personnel can remotely grant access after verifying their identity. Intercom systems provide an additional layer of security by allowing direct communication with visitors before granting access.
- Vehicle Access Control Systems: Vehicle access control systems are specifically designed to regulate vehicular traffic at entry and exit points. These systems may include vehicle barriers, automated gates, license plate recognition technology, or RFID tags for vehicles. Vehicle access control systems are commonly used in parking facilities, gated communities, and industrial sites to manage vehicle entry and enforce parking restrictions.
- Integrated Solutions: Many modern gate access control systems offer integrated solutions that combine multiple authentication methods, such as card readers with biometric scanners or keypad entry with remote control capabilities. Integrated solutions provide enhanced security and flexibility by allowing organizations to choose the most suitable authentication methods for their specific needs.
These are just a few examples of gate access control solutions available in the market, and organizations can choose the most appropriate solution based on their security requirements, budget, and operational preferences.
Key Features and Components
Effective gate access control systems incorporate several essential features to ensure robust security and efficient access management. Here are some key features:
- Authentication Methods: The system should support multiple authentication methods such as keypad entry, card readers, biometric scanners, or remote control capabilities. This allows organizations to choose the most suitable authentication method based on their security requirements and user preferences.
- Access Logs: Detailed access logs should be maintained, recording information such as date, time, and identity of individuals accessing the gate. Access logs serve as valuable audit trails for security monitoring, compliance purposes, and investigation of security incidents.
- User Management: The system should provide administrators with tools to easily manage user accounts and access permissions. This includes adding or removing users, assigning access levels, and configuring time-based or location-based access restrictions.
- 統合: Integration with other security systems and technologies, such as surveillance cameras, alarms, and building management systems, enhances overall security and enables coordinated responses to security events.
- Remote Management: Remote management capabilities allow administrators to monitor and control gate access from anywhere with an internet connection. This includes remotely granting or denying access, adjusting access permissions, and viewing access logs in real-time.
- Visitor Management: The system should include features for managing visitor access, such as temporary passes, guest credentials, or pre-registration systems. Visitor management capabilities help organizations monitor and regulate visitor traffic while maintaining security.
- Alerts and Notifications: The system should have the ability to generate alerts and notifications for unauthorized access attempts, door propping, or other security-related events. Alerts can be sent via email, SMS, or push notifications to notify administrators of potential security breaches in real-time.
- Backup and Redundancy: To ensure continuous operation and data integrity, the system should have built-in backup and redundancy mechanisms. This includes redundant power supplies, data backups, and failover capabilities to prevent system downtime or data loss in the event of hardware or network failures.
- スケーラビリティ: The system should be scalable to accommodate future growth and changes in security requirements. This includes support for adding additional gates, users, or access points without significant disruption or reconfiguration of the existing infrastructure.
- ユーザーフレンドリーなインターフェース: A user-friendly interface makes it easy for administrators to configure and manage the system effectively. Intuitive dashboards, clear navigation, and comprehensive reporting tools enhance usability and productivity.
By incorporating these essential features, gate access control systems can effectively enhance security, streamline access management, and ensure the safety of individuals and assets within controlled areas.
Type of Gate Access Control Products
HFSECURITY offers a range of gate access control products tailored to various needs and environments:
Components involved in a Typical Gate Access Control Setup
A typical gate access control setup involves several components working together to regulate entry and exit, authenticate users, and manage access permissions. Here are the key components:
- Control Panel: The control panel serves as the central hub of the access control system. It houses the necessary hardware and software to manage user credentials, process authentication requests, and control the operation of the gate or barrier. The control panel communicates with other system components to coordinate access control actions.
- Readers: Readers are devices installed at entry points to capture user credentials and initiate the authentication process. Depending on the authentication method used, readers may include:
- Card Readers: Proximity card readers, smart card readers, or key fob readers.
- Biometric Scanners: Fingerprint scanners, iris scanners, or facial recognition cameras.
- Keypads: Numeric keypads for entering PIN codes.
- Electric Locks or Gate Operators: Electric locks or gate operators are mechanisms that control the physical barrier, such as a gate, door, or turnstile. Upon successful authentication, the control panel sends a signal to the electric lock or gate operator to unlock or open the barrier, allowing authorized individuals to pass through.
- Credentials: Credentials are unique identifiers used by users to authenticate themselves to the access control system. Depending on the chosen authentication method, credentials may include proximity cards, smart cards, key fobs, PIN codes, biometric data, or mobile credentials stored on smartphones.
- Software Management System: The access control system is typically managed and configured through software installed on a computer or server. The software management system allows administrators to enroll users, define access permissions, generate access reports, and configure system settings remotely.
- 電源: A reliable power supply is essential to ensure the continuous operation of the access control system. Power is typically supplied to components such as the control panel, readers, electric locks, and other peripherals either through direct wiring or using power over Ethernet (PoE) technology.
- Communication Interface: Communication interfaces enable data exchange between various system components, allowing them to communicate with the control panel and management software. Common communication interfaces include Ethernet, Wi-Fi, RS-485, and Wiegand protocols.
- Backup Battery: To maintain functionality during power outages or emergencies, some access control systems incorporate backup batteries. These batteries provide temporary power to critical components, ensuring that the system remains operational and secure even in adverse conditions.
By integrating these components into a cohesive system, gate access control setups effectively regulate access, enhance security, and provide a seamless experience for authorized users.
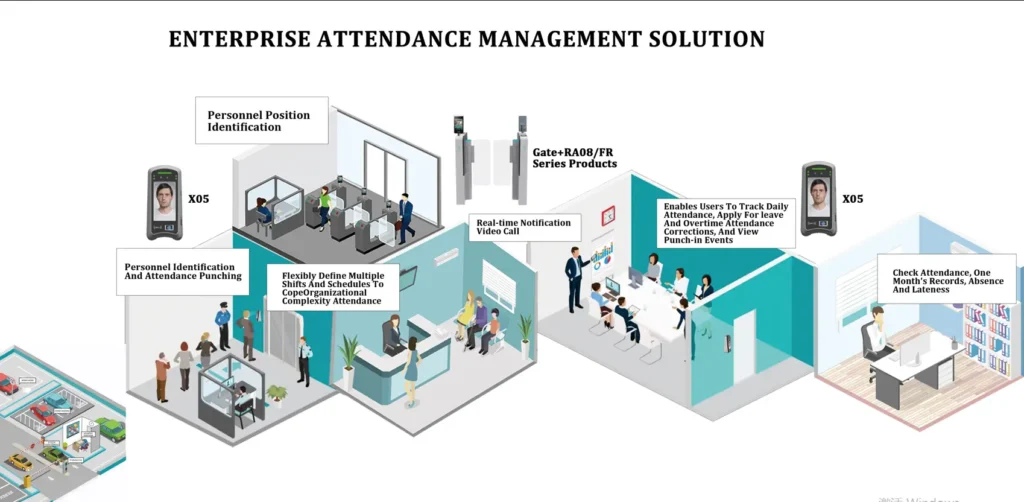
How Do Gate Security Systems Work?
Gate security systems work by utilizing various technologies and components to regulate access to a particular area. Here’s a general overview of how these systems typically function:
- 認証: When someone approaches the gate, they are required to authenticate their identity through a predefined method such as entering a PIN code on a keypad, presenting an access card or key fob to a card reader, or undergoing biometric verification like fingerprint or facial recognition.
- 検証: The system then verifies the provided credentials against a database of authorized users. If the credentials match those on record, access is granted; otherwise, entry is denied.
- Control Mechanisms: Upon successful authentication, the gate control mechanisms are activated to allow entry. These mechanisms can include electric locks that release to open the gate, barriers that lift or retract, or similar mechanisms depending on the type of gate.
- Logging and Monitoring: Gate access control systems typically maintain a log of all access events, recording details such as the date, time, and identity of individuals who accessed the area. This information is valuable for security monitoring, audit trails, and investigative purposes.
- Remote Management: Many modern gate access control systems offer remote management capabilities, allowing authorized personnel to monitor and manage access from a centralized location. This feature enables real-time adjustments to access permissions, troubleshooting of issues, and tracking of system performance.
- 統合: Gate access control systems can integrate with other security systems such as CCTV cameras, alarms, and intrusion detection systems. Integration enhances overall security by providing a comprehensive view of the protected area and enabling automated responses to security events.
Overall, gate security systems work by combining authentication, verification, control mechanisms, logging, monitoring, remote management, and integration to regulate access and enhance security at entry and exit points.
What Styles of Access Control Gates are there?
Access control gates come in various styles, each designed to suit specific security needs, aesthetic preferences, and space constraints. Here are some common styles of access control gates:
- Swing Gates: Swing gates operate similarly to traditional doors, swinging open and closed on hinges. They are commonly used in both residential and commercial settings and are available in single or double configurations. Swing gates can be automated for convenience and are suitable for properties with ample space for swinging clearance.
- Sliding Gates: Sliding gates operate horizontally along a track, sliding to the side to open and close. They are ideal for properties with limited space for swing clearance and are often used in industrial, commercial, and high-security applications. Sliding gates can be automated for efficient operation and enhanced security.
- Barrier Arm Gates: Barrier arm gates, also known as boom gates or barrier gates, feature a horizontal arm that raises and lowers to control vehicle access. They are commonly used in parking lots, toll booths, and vehicle access points where quick entry and exit are required. Barrier arm gates can be integrated with access control systems to regulate vehicle access effectively.
- Turnstile Gates: Turnstile gates consist of rotating arms or barriers that allow one person to pass through at a time. They are frequently used in high-traffic areas such as stadiums, transit stations, and office buildings to control pedestrian access. Turnstile gates can be configured with various authentication methods, including card readers, biometric scanners, and ticket validators.
- Pedestrian Gates: Pedestrian gates are designed specifically for pedestrian access control. They can range from simple swing gates to more sophisticated gates equipped with card readers, biometric scanners, or ticket validators. Pedestrian gates are commonly used in conjunction with other access control measures to secure entry points and manage pedestrian flow.
- Vertical Lift Gates: Vertical lift gates, also known as bollard gates or rising bollards, consist of vertical posts that retract into the ground to allow vehicle access. They are often used in high-security areas such as government facilities, military bases, and critical infrastructure sites. Vertical lift gates provide robust perimeter security and can withstand vehicle impact.
- Folding Gates: Folding gates, also referred to as accordion gates or scissor gates, consist of interconnected panels that fold and unfold to open and close. They are commonly used to secure storefronts, storefront windows, and warehouse entrances. Folding gates offer visibility and ventilation while providing an effective barrier against unauthorized entry.
- Cantilever Gates: Cantilever gates operate similarly to sliding gates but are supported by rollers or wheels mounted on a support structure, eliminating the need for a track along the ground. They are suitable for properties with uneven terrain or where ground clearance is a concern. Cantilever gates are known for their smooth and quiet operation.
The choice of access control gate style depends on factors such as space constraints, security requirements, aesthetic preferences, and the intended application. Property owners and security professionals should carefully evaluate these factors to select the most suitable gate style for their needs.
Types of Access Control for Gate Entry Systems
Types of access control for gate entry systems can vary based on the level of security needed, the type of property, and the preferences of the users. Here are some common types:
- Proximity Card Readers: Proximity card readers utilize radio frequency identification (RFID) technology to detect and read credentials embedded in cards or key fobs. Users hold the card or fob near the reader to gain access through the gate.
- Smartphone Apps: With advancements in technology, gate entry systems can now be controlled via smartphone apps. Users with authorized credentials can use their smartphones to remotely open gates, providing convenience and flexibility.
- 生体認証スキャナー: Biometric access control for gate entry systems utilizes unique physical characteristics such as fingerprints, iris patterns, or facial features to verify the identity of users. Biometric scanners ensure high levels of security and prevent unauthorized access.
- PIN Code Entry: Gate entry systems equipped with PIN code entry require users to input a unique numerical code on a keypad to gain access. This method is straightforward and can be easily managed by assigning individual codes to authorized users.
- Intercom Systems: Intercom systems integrated into gate entry systems allow visitors to communicate with occupants or security personnel before being granted access. This enables verification of identity and enhances security by preventing unauthorized entry.
- License Plate Recognition (LPR): LPR technology automatically reads and records license plate numbers of vehicles approaching the gate. Authorized plates are granted access while others are denied entry, providing efficient and streamlined access control.
- Remote Control Devices: Remote control devices, such as handheld transmitters or keychain remotes, allow authorized users to open gates from a distance. This method is commonly used in residential settings or gated communities for convenient access.
- Time-Based Access Control: Gate entry systems can be programmed to allow access only during specific times or days of the week. This time-based access control ensures that access is granted only when needed, enhancing security and control over the property.
- セキュリティシステムとの統合: Gate entry systems can be integrated with broader security systems, such as surveillance cameras and alarm systems, to provide comprehensive security coverage and real-time monitoring of entry points.
- Visitor Management Systems: Visitor management systems for gate entry control the entry of visitors by generating temporary access credentials or visitor passes. These systems help track and manage visitor access while ensuring the security of the premises.
The choice of access control for gate entry systems depends on factors such as security requirements, user convenience, and the specific needs of the property or organization. Integrating multiple access control methods may offer layered security and enhanced flexibility in managing gate access.

Benefits of Gate Access Control Solutions:
Gate access control solutions offer numerous benefits for properties and organizations, including:
- 強化されたセキュリティ: Gate access control systems provide a robust barrier against unauthorized entry, helping to prevent intrusions, theft, vandalism, and other security threats. By restricting access to authorized personnel and vehicles, these systems significantly enhance the overall security of the premises.
- Improved Safety: Access control gates help regulate the flow of traffic, both pedestrian and vehicular, within the property, reducing the risk of accidents and improving overall safety. They can also prevent unauthorized individuals from accessing hazardous areas or restricted zones, further enhancing safety measures.
- Convenience and Efficiency: Automated gate access control systems offer convenience and efficiency by allowing authorized users to enter and exit the premises seamlessly without the need for manual intervention. This saves time and effort for both occupants and security personnel, particularly in high-traffic environments.
- Customization and Flexibility: Gate access control solutions can be tailored to meet the specific security needs and operational requirements of different properties and organizations. From choosing the appropriate gate style to integrating various access control methods, customization options offer flexibility in designing a system that best suits the unique needs of the premises.
- Visitor Management: Gate access control systems enable effective visitor management by providing mechanisms for screening and verifying the identity of visitors before granting them access. This helps maintain security while accommodating legitimate visitors and ensuring a smooth entry process.
- Auditing and Reporting: Many gate access control systems are equipped with auditing and reporting features that log access events, including entry and exit times, user credentials, and any security incidents. These reports provide valuable insights for security monitoring, compliance, and incident investigation purposes.
- スケーラビリティ: Gate access control solutions are scalable, allowing for easy expansion or modification as the needs of the property or organization evolve over time. Whether adding new access points, integrating additional security features, or accommodating growing user volumes, scalable systems can adapt to changing requirements.
- 他のシステムとの統合: Gate access control systems can be seamlessly integrated with other security systems, such as surveillance cameras, alarm systems, and intercoms, to create a comprehensive security infrastructure. Integration enhances situational awareness, facilitates real-time monitoring, and improves overall security effectiveness.
- コスト削減: While initial investment costs may be involved in implementing gate access control solutions, they can result in long-term cost savings by reducing security risks, minimizing losses from theft or vandalism, streamlining operational processes, and potentially lowering insurance premiums.
- Legal and Regulatory Compliance: Gate access control systems help properties and organizations comply with legal and regulatory requirements related to security, access control, and data protection. By implementing robust access control measures, they demonstrate a commitment to safeguarding assets, information, and the safety of individuals.
Overall, gate access control solutions offer a comprehensive approach to security management, combining technology, automation, and customization to create a secure and efficient environment for occupants, visitors, and assets.
Applications and Use Cases:
Gate access control solutions find applications across various industries and settings where security, safety, and access management are paramount. Some common applications and use cases include:
- 住宅コミュニティ: Gated residential communities utilize gate access control systems to regulate entry and exit, ensuring only residents and authorized visitors can access the premises. These systems enhance security and provide peace of mind to residents by preventing unauthorized individuals from entering the community.
- Commercial Properties: Office buildings, corporate campuses, and commercial complexes employ gate access control solutions to secure entrances and restrict access to authorized personnel. These systems help protect valuable assets, sensitive information, and ensure the safety of employees and visitors.
- 産業施設: Industrial facilities, such as manufacturing plants, warehouses, and distribution centers, rely on gate access control systems to manage entry and exit points, control vehicle traffic, and prevent unauthorized access to critical areas. These systems enhance security, improve operational efficiency, and ensure compliance with safety regulations.
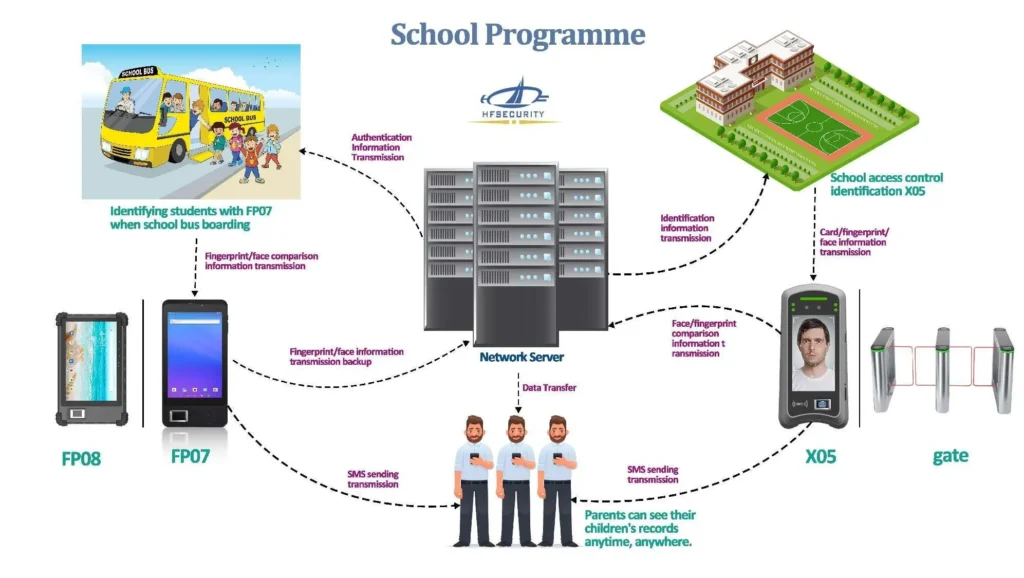
- 教育機関: Schools, colleges, and universities implement gate access control solutions to enhance campus security and control access to academic buildings, dormitories, and other facilities. These systems help prevent unauthorized entry, protect students and staff, and facilitate efficient visitor management.
- 医療施設: Hospitals, clinics, and healthcare centers utilize gate access control systems to regulate access to medical facilities, patient areas, and sensitive information. These systems help maintain patient confidentiality, prevent unauthorized individuals from entering restricted areas, and ensure the safety of patients and staff.
- Government and Military Installations: Government buildings, military bases, and other secure facilities rely on gate access control solutions to safeguard classified information, protect personnel, and control access to restricted areas. These systems play a crucial role in national security and defense by preventing unauthorized intrusion and ensuring compliance with strict security protocols.
- Retail and Commercial Establishments: Retail stores, shopping malls, and commercial establishments use gate access control systems to manage entry points, prevent theft, and enhance customer safety. These systems help regulate foot traffic, control access to restricted areas, and deter criminal activity, thereby safeguarding assets and improving overall security.
- 駐車場: Parking garages, lots, and structures employ gate access control solutions to manage vehicle entry and exit, control parking access, and enforce parking regulations. These systems help optimize parking space utilization, prevent unauthorized parking, and enhance security for vehicles and patrons.
- Entertainment Venues: Sports stadiums, concert halls, and entertainment venues utilize gate access control systems to ensure orderly entry, manage crowd flow, and enhance security during events. These systems help maintain crowd safety, prevent unauthorized access to restricted areas, and facilitate efficient ticketing and entry processes.
- Data Centers and IT Facilities: Data centers, server rooms, and IT facilities implement gate access control solutions to protect sensitive equipment, servers, and data infrastructure from unauthorized access and security breaches. These systems help ensure data integrity, prevent physical tampering, and maintain regulatory compliance in the handling of sensitive information.
These are just a few examples of the diverse applications and use cases of gate access control solutions across different industries and settings. By providing effective security, access management, and operational efficiency, these systems play a vital role in safeguarding assets, protecting individuals, and ensuring the smooth functioning of various environments.
How to select gate access control?
Selecting the right gate access control system involves thorough assessment and consideration of various factors tailored to your specific needs and environment. Here’s a step-by-step guide to help you navigate the selection process:
- Assess Security Needs: Evaluate the security requirements of your premises. Consider factors such as property size, location, potential threats, and the value of assets or information you need to protect.
- Define Access Control Methods: Determine which access control methods align with your security needs and operational preferences. Options include keypads, proximity cards, biometric readers, mobile credentials, or a combination of these methods.
- Consider Integration: Check compatibility with existing security systems like surveillance cameras, alarms, and intercoms. Seamless integration enhances overall security effectiveness and simplifies management.
- Evaluate Scalability: Choose a solution that can scale as your needs evolve. Ensure it can support additional access points, users, and functionalities as your property or organization grows.
- Establish User Authentication: Define clear protocols for user authentication and authorization. Establish access levels and permissions based on roles and responsibilities within your organization.
- Develop Visitor Management Procedures: Implement procedures for screening and registering visitors. This includes issuing temporary credentials, recording visitor information, and monitoring their activities while on-site.
- Provide Training: Ensure comprehensive training for users, security personnel, and administrators on system usage, emergency protocols, and troubleshooting. Promote awareness of security policies and best practices.
- Ensure Compliance: Stay compliant with relevant regulations and standards governing security, access control, data protection, and privacy. Regularly review and update procedures to maintain compliance.
- Plan Maintenance: Establish maintenance procedures and service agreements to ensure system reliability. Regularly inspect equipment, perform updates, and address technical issues promptly.
- Conduct Cost-Benefit Analysis: Evaluate the investment required against the expected security benefits and operational efficiencies. Consider upfront costs, ongoing expenses, potential savings, and overall ROI.
By following these steps and tailoring your approach to your specific needs, you can select a gate access control system that effectively enhances security, streamlines access management, and supports your operational objectives.
How to Use Gate Access Control
Using gate access control systems typically involves the following steps:
- User Authentication: Users approach the gate access point and authenticate themselves using the designated method, such as presenting a key card, entering a PIN code on a keypad, or scanning a biometric identifier like a fingerprint.
- Authorization Verification: Once authenticated, the system verifies the user’s authorization level based on predefined access permissions stored in the system. This step ensures that only authorized individuals are granted access to the secured area.
- Gate Operation: If the user’s authentication and authorization are approved, the gate access control system triggers the opening mechanism, allowing the user to pass through the gate.
- Monitoring and Logging: The system may log details of each access attempt, including the user’s identity, date, and time of access, and any relevant security information. This data can be useful for monitoring access patterns, detecting anomalies, and conducting audits.
- Visitor Management: For visitors, the process may involve registration at a designated location, issuance of temporary credentials, and escorting by authorized personnel while on the premises.
- Emergency Protocols: Users should be aware of emergency procedures, such as how to request emergency access or override the gate control system in case of emergencies or system failures.
- System Maintenance: Regular maintenance and monitoring of the gate access control system are essential to ensure continued reliability and security. This includes checking equipment functionality, performing software updates, and addressing any technical issues promptly.
By following these steps and ensuring proper training and awareness among users, gate access control systems can effectively enhance security and streamline access management within a property or organization.
Future Trends and Innovations:
Future trends and innovations in gate access control systems are likely to focus on enhancing security, improving user experience, and leveraging advanced technologies. Here are some anticipated developments:
- Biometric Advancements: Biometric authentication methods, such as facial recognition and iris scanning, will become more prevalent, offering higher accuracy and convenience compared to traditional methods.
- Mobile Access: The use of smartphones as access credentials will continue to rise, allowing users to open gates using mobile apps or digital keys. This trend enhances convenience and security by eliminating the need for physical cards or key fobs.
- クラウドベースのソリューション: Cloud-based access control systems will gain popularity due to their scalability, flexibility, and remote management capabilities. They allow administrators to control access from anywhere and easily integrate with other cloud-based security solutions.
- AI and Machine Learning: Integration of AI and machine learning algorithms will enable gate access control systems to analyze access patterns, detect anomalies, and adapt security protocols in real-time. This helps in preventing unauthorized access and enhancing overall security.
- IoT Integration: Gate access control systems will increasingly connect with other IoT devices and sensors, such as surveillance cameras and motion detectors, to create a comprehensive security ecosystem. This integration enables automated responses to security events and enhances situational awareness.
- Blockchain Technology: The use of blockchain for access control systems may increase, providing enhanced security through decentralized and tamper-proof access records. Blockchain can also streamline identity verification processes, especially in multi-tenant environments.
- 予測メンテナンス: Systems equipped with predictive maintenance capabilities will monitor equipment health in real-time and anticipate potential failures before they occur. This proactive approach reduces downtime and ensures continuous operation.
- Eco-Friendly Solutions: The development of energy-efficient and environmentally friendly access control systems will become more important. This includes the use of solar-powered gates, low-power components, and recyclable materials.
- Integration with Smart Cities: Gate access control systems will integrate with broader smart city initiatives, facilitating traffic management, public safety, and emergency response. This integration improves urban efficiency and security.
- Enhanced User Experience: Focus will be on making access control systems more user-friendly and intuitive. This includes features such as voice commands, touchless interfaces, and personalized settings.
By staying abreast of these emerging trends and adopting relevant technologies, organizations can ensure their gate access control systems remain effective, efficient, and future-proof.
結論:
Gate access control systems play a crucial role in enhancing security, managing access, and providing convenience in various environments, including residential, commercial, and industrial properties. By following the standard steps for using and managing these systems—such as authentication, authorization verification, and monitoring—organizations can maintain secure and efficient access control.
HFSecurity is a well-known manufacturer specializing in gate access control systems. Our products range from RFID card readers to biometric access control devices, designed to regulate entry and exit points in various settings such as residential complexes, commercial buildings, and government facilities. With a focus on security, reliability, and user-friendly interfaces, HFSecurity’s solutions are widely used globally. We offer a diverse range of access control products tailored to different needs and environments, ensuring efficient and secure management of entry points.
Frequently Asked Questions (FAQ) about Gate Access Control
What is gate access control?
Gate access control refers to the technology and systems used to regulate entry and exit points, typically at gates or barriers. These systems authenticate and authorize individuals, vehicles, or objects to enter or exit a controlled area, enhancing security and controlling access.
How does gate access control work?
Gate access control systems typically use various authentication methods such as RFID cards, biometric scans (like fingerprint or facial recognition), PIN codes, or even remote access through smartphones. When an individual or vehicle approaches the gate, they present their credentials to the access control device, which then verifies the credentials against a database and grants access if authorized.
What are the benefits of gate access control systems?
Gate access control systems offer several benefits including enhanced security by restricting unauthorized access, improved accountability through access logs and audit trails, increased convenience with automated entry processes, and better management of visitor access.
Where are gate access control systems commonly used?
Gate access control systems are commonly used in a wide range of settings including residential communities, commercial buildings, industrial facilities, educational institutions, government installations, parking lots, and gated communities.
What types of gate access control devices are available?
Gate access control devices vary based on authentication methods and features. Common types include RFID card readers, keypads for PIN entry, biometric scanners, vehicle barrier arms, and remote access systems.
Can gate access control systems integrate with other security systems?
Yes, gate access control systems can often integrate with other security systems such as surveillance cameras, intercoms, alarm systems, and visitor management software to provide comprehensive security solutions.

