What is Iris Recognition?
Reconnaissance de l'iris is a biometric authentication method that identifies individuals based on the unique patterns of their iris—the colored ring around the pupil. Unlike fingerprints or facial features, the iris remains stable throughout a person’s life, making it highly reliable for identification. The process involves capturing an image of the iris using specialized cameras and converting it into a digital template for comparison.
How is Iris Recognition Applied?
Iris recognition is widely used in:
1.Security Systems
Airports, government facilities, and corporate offices use iris recognition for secure, contactless access control.
With its unmatched accuracy, iris recognition relies on unique eye patterns, providing a high level of security. This technology ensures only authorized individuals can gain access to restricted areas, offering both enhanced protection and operational efficiency. It’s the ideal solution for high-security environments where precision and hygiene are critical.
2.Smartphones
Samsung Galaxy’s iris scanning uses infrared to map 240+ iris patterns with 1 in 1M accuracy. This touchless tech works in darkness, resists spoofing, and authenticates in <1 second. Though newer models use ultrasonic sensors, iris scanning set the standard for mobile security.
3.Healthcare
Iris scanning enables secure patient identification and medical record access by authenticating unique eye patterns with 1 in 1M accuracy. This touchless system prevents unauthorized access while complying with HIPAA standards, ideal for sterile environments like operating rooms. Faster than passwords and more hygienic than fingerprint scanners, it streamlines workflows for healthcare professionals.
4.Banking
Iris recognition is increasingly used for fraud prevention in transactions and ATM authentication, offering a secure and reliable solution.
By using unique iris patterns for identification, this technology significantly reduces the risk of fraud, ensuring that only the rightful account holder can access and approve transactions. It provides a fast, contactless, and highly accurate method for ATM authentication and secure financial transactions, boosting both security and user confidence.
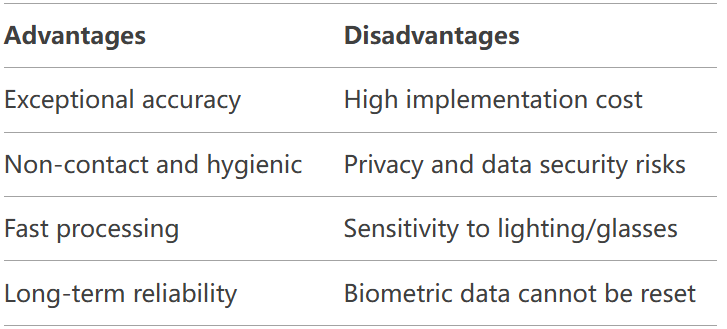
Advantages of Iris Recognition
1.High Accuracy
The probability of two irises being identical is nearly zero, making iris recognition one of the most reliable biometric methods.
Each person’s iris has unique patterns that are highly stable over time, ensuring that the chances of false matches are extremely low. This unparalleled level of accuracy makes iris recognition ideal for secure identification in sensitive applications like access control, banking, and authentication, providing confidence in both security and precision.
2.Non-Contact
Contactless iris recognition eliminates surface contact, reducing germ transmission in high-traffic areas. Users authenticate in seconds without touching shared devices – ideal for hospitals, labs, and public kiosks. This hygienic solution combines security with convenience, preventing bacterial spread while maintaining 1 in 1M accuracy.
3.Speed
Iris recognition authenticates users in under 2 seconds – perfect for busy airports. This frictionless flow processes 500+ passengers/hour without bottlenecks, while maintaining 1 in 1M accuracy. No queues, no touchscreens, just seamless security that keeps traffic moving.
4.Durability
Unlike fingerprints that wear or facial features that age, iris patterns stay stable for life. This makes iris recognition uniquely reliable for long-term security systems – your authentication stays consistent from enrollment to decades later, with no need for re-registration.
Disadvantages of Iris Recognition
1.Cost
While iris recognition offers unmatched accuracy, its hardware costs 2-3× more than fingerprint or facial recognition systems. High-end infrared cameras, anti-spoofing sensors, and specialized processors drive the price premium. However, for high-security applications like border control or banking, the long-term reliability and fraud prevention justify the investment.
2.Privacy Concerns
Storing biometric data, such as fingerprints or facial scans, raises significant risks of misuse or data breaches. If such sensitive information is accessed by unauthorized parties, it could lead to identity theft, fraud, or other malicious activities, making strong security measures essential for protecting this data.
3.Environmental Sensitivity
Bright lighting or reflective surfaces, such as glasses, may interfere with the scanning process by creating glare or obscuring key features needed for accurate recognition. This can lead to reduced performance or failure to properly identify individuals, especially in facial or iris recognition systems.
4.Irreversible Data
If compromised, iris templates cannot be “reset” in the same way passwords can. Unlike passwords, which can be changed or reset, iris data is uniquely tied to an individual and cannot be altered. This makes the security of iris recognition crucial, as compromised templates cannot be replaced.
Applications of Iris Recognition Technology
Gouvernement
Border control and national ID programs.
Corporate Security
Restricted-area access for employees.
Healthcare
Patient identification and prescription management.
Banking
Secure ATM withdrawals and mobile banking.
Iris Recognition: Pros and Cons at a Glance
FAQ
Iris recognition analyzes the iris’s surface patterns, while retinal scanning maps blood vessels in the retina. The latter is more invasive and less common.
Modern systems use 3D imaging and liveliness detection to prevent spoofing with photos or videos.
Yes—iris patterns form by age two and remain stable, making it suitable for minors.
High costs and privacy debates limit its scalability compared to fingerprint or facial recognition.
Conclusion
Reconnaissance de l'iris offers a secure and efficient solution for identity verification, with applications spanning security, healthcare, and finance. However, challenges like cost and privacy concerns must be addressed for broader adoption. As technology evolves, iris recognition may become a cornerstone of next-generation authentication systems—balancing innovation with ethical responsibility.

